BlueCat Infrastructure Assurance 8.4 boosts AI capabilities with anomaly detection
BlueCat Infrastructure Assurance, previously known as Indeni, has been providing Artificial Intelligence capabilities even before the recent hype in the matter. Today, we’re excited to announce our next step in the AI journey – Anomaly Detection.
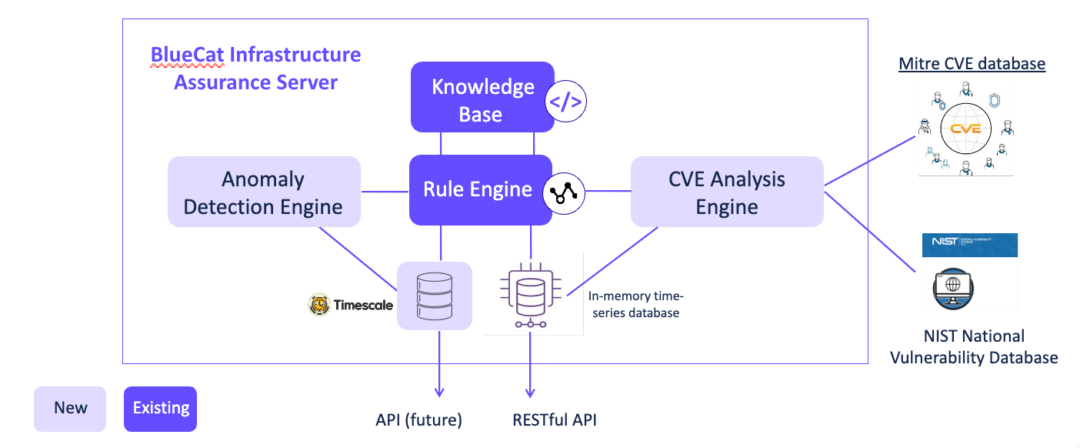
In this release we have included several new components:
- An Anomaly detection engine
- An embedded long-term time-series database (Postgresql timescaledb)
- A CVE analysis engine
Anomaly detection
The anomaly detection engine uses machine learning models to identify outliers and unusual behaviors for a number of metrics in your Palo Alto Networks NGFW and BlueCat BDDS devices. Upon detection of an anomaly, a warning alert is generated.
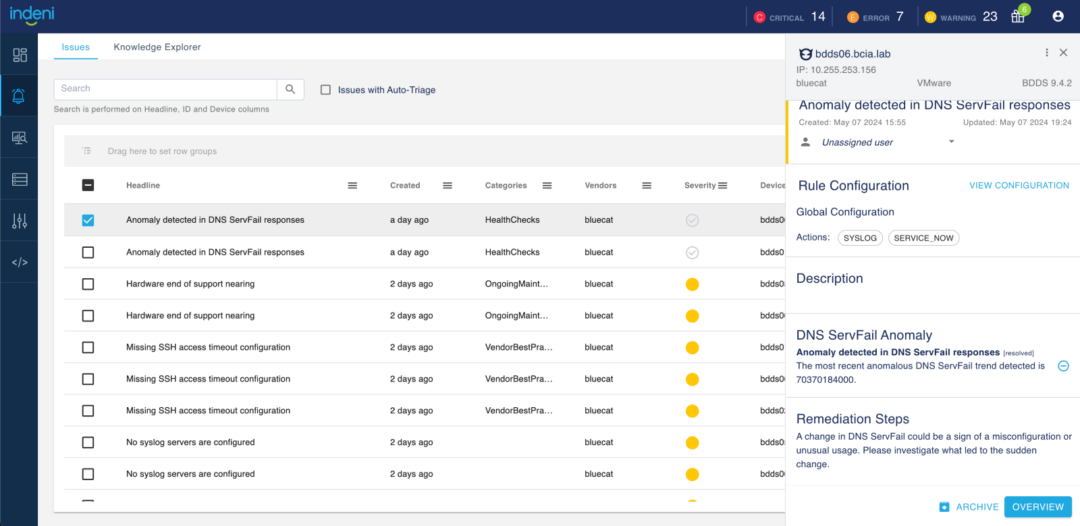
Awareness of such anomalies identifies early symptoms to emerging issues, allowing you to address them before they become bigger problems. In our implementation, we’re using the popular z-score method to detect anomalies. A z-score measures exactly how many standard deviations above or below the mean a data point is. The system evaluates several metrics (see below) based on a week’s worth of data points. These data points are stored in the newly embedded time-series database. When a new data point is collected, a z-score is calculated. An alert is generated if the z-score of that data point is greater than 3 (or less than –3). The alert will remain active for 10 minutes. During that time, if no other anomalies are detected, the alert will resolve itself and go into the cooldown state. If another data point has a z-score greater than 3 (or less than –3), the alert will remain active for another 10 minutes.
There is plenty of literature out there on z-score, so I won’t go into details on how z-score is calculated. Instead, we’ll look at what metrics we’re applying to the models to detect outliers and why they’re important.
Anomalies for Palo Alto Networks NGFW
The Palo Alto Networks firewall keeps a count of all drops and what causes them. Analyzing these drop counters provides insights into the processes, packet flows and sessions on the firewall. Four global drop counters are analyzed for anomaly detection.
1/ flow_tcp_non_sync_drop
If this drop counter increases suddenly and significantly, it is indicative of asymmetric routing in your environment. Applications will encounter issues. For example, websites are only loading partially or applications simply not working.
2/ Flow_policy_deny
This counter flow_policy_deny increments when the session setup for a traffic is denied by a security policy. If an abnormal increase in this counter is detected, it could mean a misconfigured rule, a scanner on the network, increased attempted connections from a rogue device, etc.
3/ flow_action_close
The firewall sends a TCP Reset (RST) when a threat is detected in the traffic flow. The flow_action_close global counter tracks the number of TCP sessions closed via injecting RST. A sudden increase in this counter can potentially pose a security risk so you want to investigate immediately.
4/ nat_xlat_address_resolved_fail
This global counter provides information about the total number of times when FQDN resolve failed. If nat_xlat_address_resolved_fail suddenly spikes, this could mean there is a problem with resolving DNS on the firewall.
Anomalies for BlueCat Integrity
The new anomaly alert is “A sudden increase in SERVFAIL”. SERVFAIL errors may be caused by a temporary server overload situation or a temporary connectivity disruption. A small number of SERVFAIL errors may not be alarming, but a spike in SERVFAIIL can mean a combination of many issues that can lead to bigger problems. For example, it may be a technical problem with your DNS servers, or firewalls blocking users from going to a domain, or DNSSEC verification failures. These issues have the potential to cause downtime for a substantial number of domains, users or both. An investigation is warranted!
Note: This feature is disabled by default. Please create a ticket. Our support team will work with you to enable it. Since this is the first release, we want to ensure that you’ve the resources to support the new capability.
Identify common vulnerabilities and exposures
A recent report from Coalition indicates an anticipated 25% rise in the total count of published common vulnerabilities and exposures for 2024. The sharp CVE increase heightens security concerns and puts tremendous pressure on an already overloaded security team, making automation essential.
We’re excited to release our CVE analysis engine which provides a network device’s vulnerability analysis. The engine automatically compares the CVE information from the MITRE CVE database and the NIST National Vulnerability Database (NVD) with OS versions running on the devices in your network. Based on this comparison, it will automatically generate alerts for devices exposed to certain CVEs.
Imagine the possibility of receiving alerts about new CVEs near real time that are impacting your environment. Coupled with the new system-defined CVE report, you can get a list of devices with vulnerabilities categorized by severity just a click away. We recommend that you run this report after every upgrade to pick up new CVE’s impacting your environment.

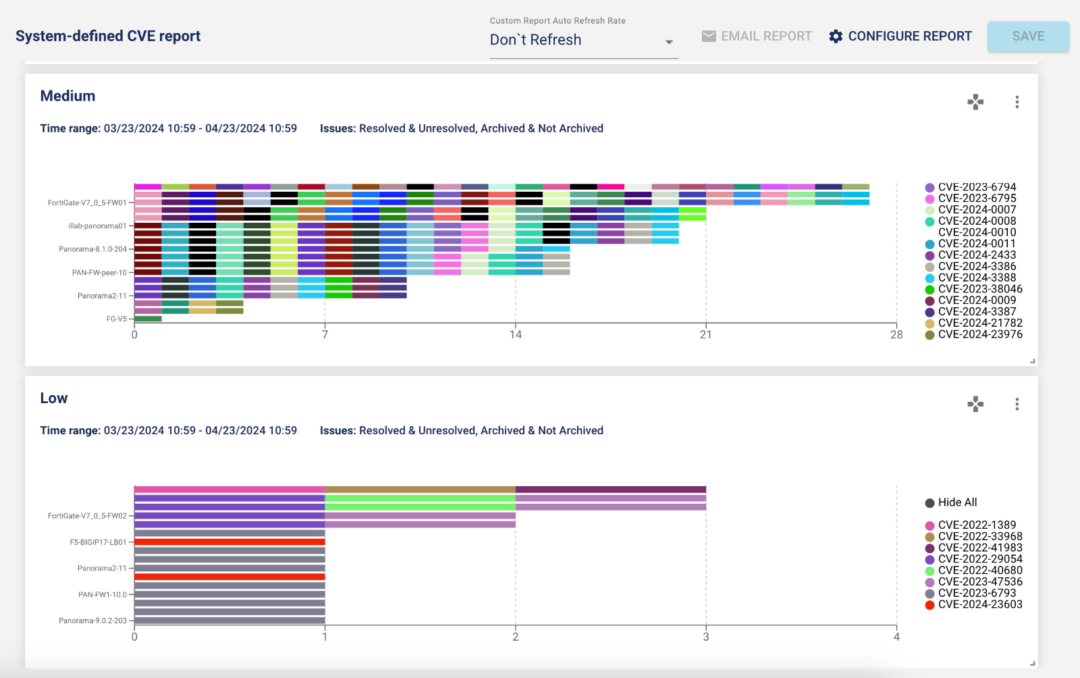
The new engine brings 200+ alerts to the release. The support includes Blue Coat CAS & ProxySG, Check Point secure gateways, Cisco ASA, F5 LTM, Fortinet FortiGate firewalls and Palo Alto Networks NGFW. The CVE’s covered as those dated from 2022 on.
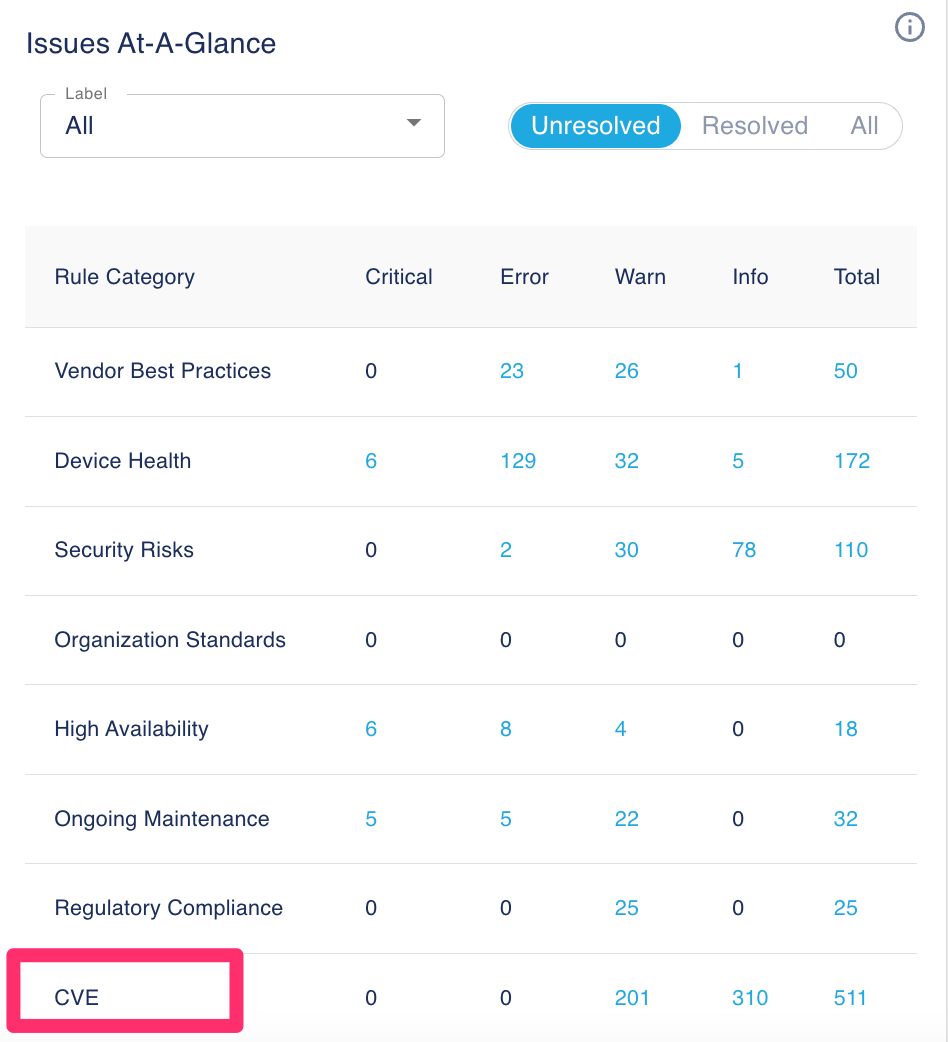
With so many new rules, we didn’t want to overwhelm the Issues page. We created a new rule category called CVE consisting of these 200+ rules. By design, the Issues page and the Knowledge Explorer page exclude rules from the CVE category. To see rules in the CVE category, reset the default filters by selecting CVE in the Categories column.
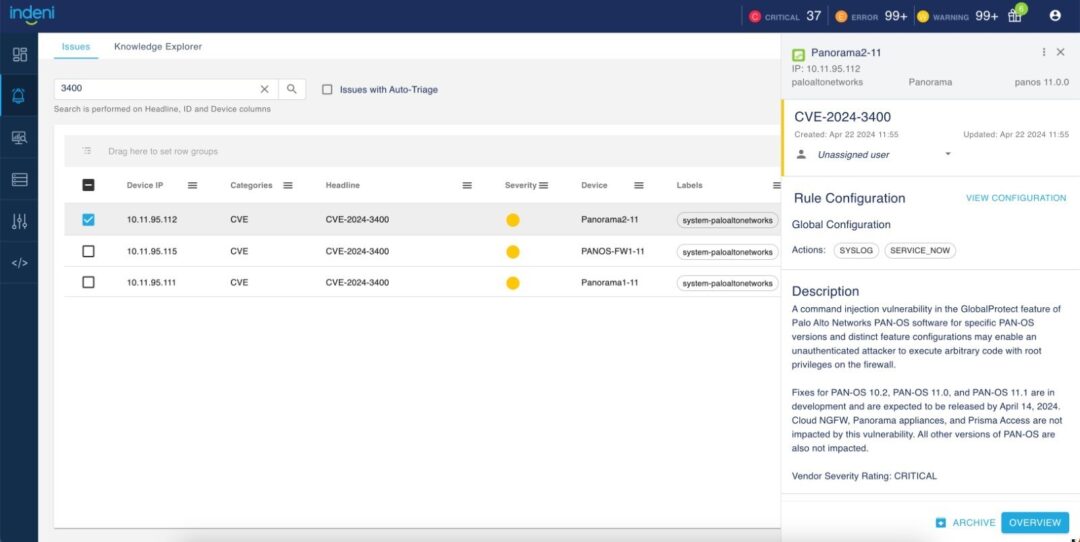
The new rule headline shows the CVE ID (CVE-2024-xxx). The description consists of details about the vulnerability. Note: we’ve deprecated the old CVE rules.
With the new rule category CVE, an additional benefit is that you can now navigate to your CVE alerts from the Issues-At-A-Glance widget from the analytics dashboard.
Custom reports
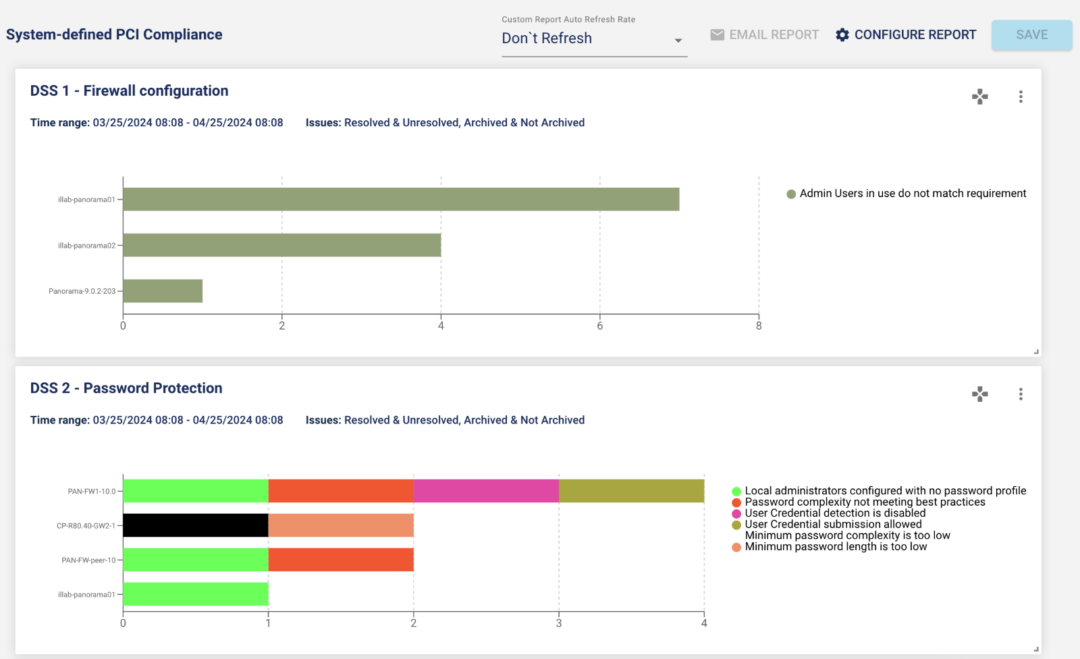
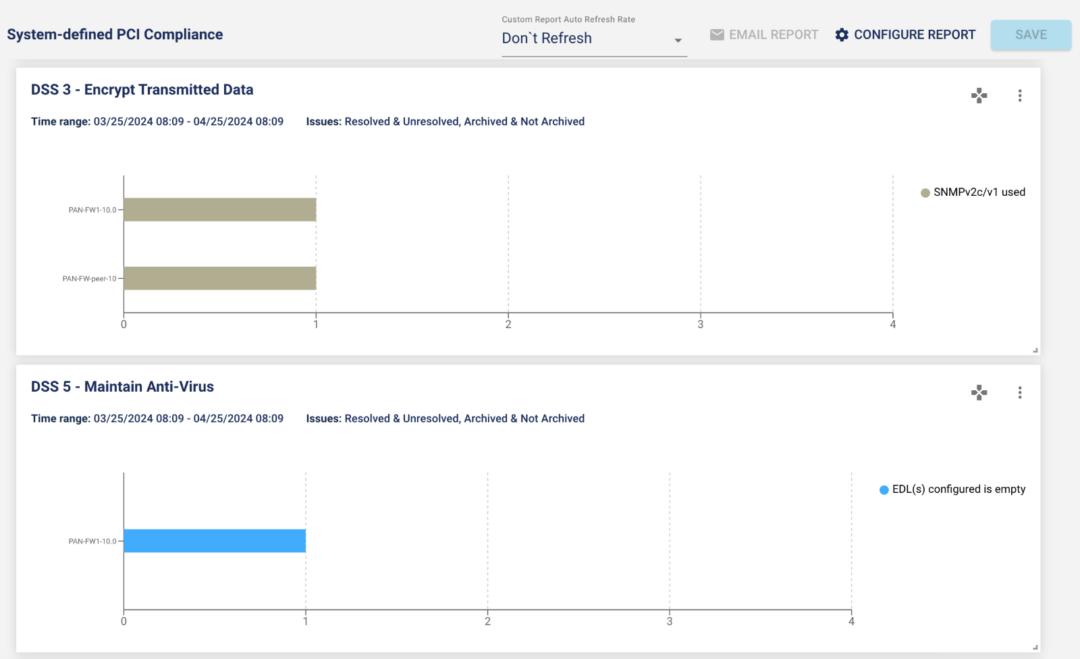
#1 – System-defined PCI compliance report
A new out-of-the-box Payment Card Industry Data Security Standard (PCI DSS) report is introduced in this release. We have over 100 rules that are mapped to the PCI compliance standard.

2 – Legend improvements
You can now change the legend and save it in your report. The new ‘Hide All’ option in the legend makes it easy for you to hide some of the attributes in your graph.
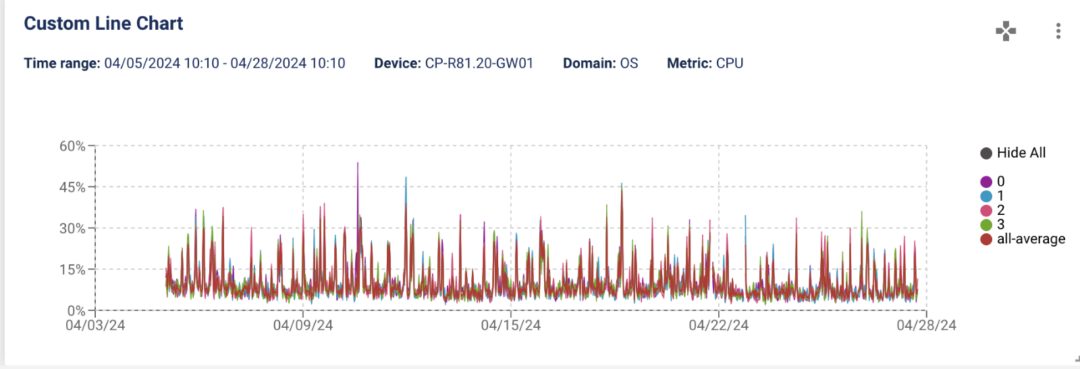
You can now change the legend and save it in your report.

Email notification for every issue item
Alert fatigue is real. BlueCat Infrastructure Assurance keeps noise levels down without letting problems escape you. Issue item is one of the techniques to reduce noise. A great example is VPN tunnels. A firewall typically has many VPN tunnels connecting remote sites and users. Instead of alerting you on every VPN tunnel down event, we associate a tunnel as an issue item. When the first VPN tunnel goes down, we create a new issue. When the second VPN tunnel goes down, we add the 2nd VPN tunnel down event as an issue item to the existing alert.
With 8.4, you can disable issue item collection by changing the configuration file. Instead of concatenating issue items to an existing alert, the system generates a new alert for every issue item. This means that enabling this feature can greatly increase the number of alerts in your environment.
Knowledge
We added over 200 Auto-Detect elements and enhancements in this release for BlueCat Integrity, Broadcom/Symantec/Blue Coat Content Analysis, Check Point Maestro, Palo Alto Networks Gateway, etc. For a complete list of enhancements, see details in the release notes.