3.9 CVE Analysis
In 8.4, we introduced a CVE analysis engine which provides a network device’s vulnerability analysis. The engine automatically compares the CVE information from the MITRE CVE database and the NIST National Vulnerability Database (NVD) with OS versions running on the devices in your network. Based on this comparison, it will automatically generate alerts for devices exposed to certain CVEs.
Couple with the new system-defined CVE report, you can get a list of devices with vulnerabilities categorized by severity just a click away. See System-defined reports in 4.1 Custom Reports for a sample report. We recommend that you run this report after every upgrade to pick up new CVE’s impacting your environment.
The new engine brings 200+ alerts to a release. The support includes Blue Coat CAS & ProxySG, Check Point secure gateways, Cisco ASA, F5 LTM, Fortinet FortiGate firewalls, Palo Alto Networks NGFW, just to name a few. The CVE’s covered as thos dated from 2022 onl
With so many new rules, we didn’t want to overwhelm the Issues page. We created a new rule category called CVE consisting of these 200+ rules. By design, the Issues page and the Knowledge Explorer page exclude rules from the CVE category. To see rules in the CVE category, reset the default filters by selecting CVE in the Categories column
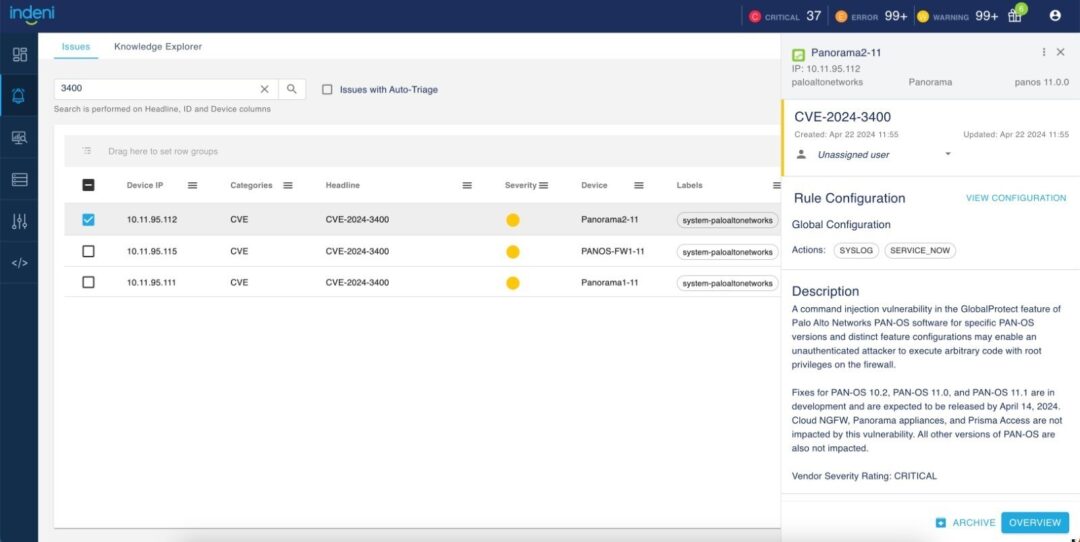
The new rule headline shows the CVE ID (CVE-2024-xxxx). The description consists of details about the vulnerability.
Note: CVE rules prior to 8.3 have been deprecated.
With the new rule category CVE, an additional benefit is that you can now navigate to your CVE alerts from the Issues-At-A-Glance widget from the analytics dashboard.
Every release, we will retrieve new rules from the MITRE CVE database and the NIST NVD. New rule will be generated for the system-defined CVE report.